SECURITY TESTING SERVICES
Security trying out has ended up a truly crucial a part of an employer’s improvement strategy. This is due to the growth in the number of privacy breaches that companies are dealing with nowadays. To cope efficiently with our client’s protection trying out desires, TGGTECH adopts the state-of-the-art enterprise standards and testing methodologies.
TGGTECH possesses rich information on Security Testing of enterprise packages, catering to varied commercial enterprise desires. TGGTECH has tremendous enjoy in serving clients across exceptional enterprise verticals and enterprise sizes. Our Web application penetration checking out uncovers vulnerabilities in packages and ensures the software risks are minimized. Also, our code analyzers make sure your software code is benchmarked for multiplied quality assurance. TGGTECH’s key differentiators consist of:
SECURITY TESTING CENTER OF EXCELLENCE
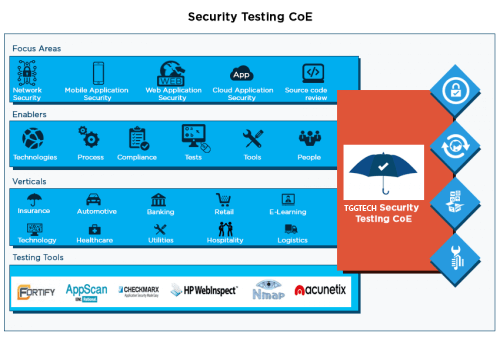
TGGTECH has a dedicated Security Testing Center of Excellence (TCoE) that has advanced methodologies, tactics, templates, checklists, and recommendations for net programs, software program products, networks, and cloud. TGGTECH gives end-to-cease safety testing offerings inclusive of Network Penetration Testing, SCADA Network Vulnerability Assessment and Penetration Testing, Web Application Penetration Testing, Wireless Network Assessment and Penetration Testing. This practice consists of over 100 security checking out experts who preserve certifications which include Certified Ethical Hacker (CEH) and Certified Security Analyst (CSA). This group continuously researches the brand new threats/vulnerabilities being pronounced together with new equipment/strategies to pick out those problems. As part of this attempt, the group has conducted proactive vulnerability assessments for websites like Amazon and PayPal. TGGTECH’s safety testing group has also been diagnosed using those companies for the vulnerabilities said. As a result of the research conducted with the aid of this crew, the CoE has constructed up a repository of safety test instances/checklists and developed capabilities the usage of open supply and proprietary protection checking out equipment.
TGGTECH’s Security TCoE includes dedicated groups of safety testing experts with broad expertise spanning a couple of domains/industries, current technological resources/gear. Also, our ISO 27001 and ISO 9001 certified procedures help make certain we deliver world magnificence protection testing offerings for our clients to help them live compliant with the pains of compliance-driven businesses.
TGGTECH’S SECURITY TESTING SERVICES OVERVIEW
TGGTECH’s check professionals deliver comprehensive revel in across domain names and technologies. They use a four-pronged technique which includes choosing the right enablers, methods, reporting models and tools to discover defects early within the test existence cycle and boost up a time to market.
TGGTECH’s Security testing offerings deal with mission-crucial protection challenges faced using firms. With critical consciousness on areas such as Network security, Mobile utility safety, Cloud software safety, and Source code evaluation, our 5 step safety test lifecycle makes your programs secure.
We have deep expertise in providing Security testing services to our global enterprise clients. The image represents a snapshot of our security testing services.
To recognize more significant about the precise nature of the safety testing offerings we provide, browse the categories under.
What Clients Says
Contact Us
Consult our experienced team of career testers for your Testing requirements.
TGGTECH’S SECURITY TESTING OFFERINGS
Is Global Leader in Independent Software Testing Services World’s 1st Independent Software Testing Services Company.Application Security Testing
Mobile Application Security Testing
Network Penetration Testing
Cloud Application Security Testing
SECURITY TESTING TYPES & TECHNIQUES
Over the last few years, TGGTECH has built up a repository of security test cases and developed capabilities using both open source and proprietary security testing tools.
Security Testing Techniques: TGGTECH implements great-of-breed strategies to check for SQL injection, Cross Site Scripting, Cross Site Request Forgery (CSRF) (consists of the Top Ten OWASP) and 0-day vulnerabilities along with vulnerabilities discovered by using our R&D group via CoE. TGGTECH’s method consists of test strategies that are manually carried out, for example, domain/enterprise logic pushed assessments that are then translated into manually crafted payload to evaluate the vulnerabilities and show off steps that can take advantage of any weak spot inside the Information/Network device.
Testlets for various types of Security Testing: TGGTECH has collated Test-lets based totally on diverse security check types which might be hired for Security testing. The tests include checking out for vulnerabilities which include SQL Injection, Cross-Site Scripting, Broken Authentication and Session Management, Unsecure Direct Object Reference, Cross-Site Request Forgery, Security Misconfiguration, Unsecure Cryptographic Usage, Failure to Restrict URL Access, Insufficient Transport Layer Protection, and Invalidated Redirects and Forwards.
SECURITY TESTING DASHBOARDS
TGGTECH’s Security Testing Dashboard includes a comprehensive file outlining the vulnerabilities found all through the cycle together with additional records including screenshots and replica steps to facilitate ease of know-how. The vulnerabilities detected are scored with admire to enterprise preferred CVSS 3.0 framework.
This comprehensive document will incorporate an govt summary file for top control and technical committee to exhibit the safety posture of application in conjunction with the distinctive vulnerability record which incorporates vulnerability details and feasible recommendations aimed in the direction of mitigation.
Security Assessment record of software is split into different sections to facilitate easy clarity. Reports start with an Executive tear-off to facilitate easy reference of assessment findings to executive management and feature an govt summary imparting a summarized view of the overall protection posture of the utility assessed. Customers can discern out average security posture based on the test consequences. This segment also lists remember of vulnerabilities by way of their score and severity.
KEY DIFFERENTIATORS OF TGGTECH’S SECURITY TESTING SERVICES
TGGTECH’s Security Testing Services (Application Penetration Services) has continuously met and exceeded the needs of establishments and ISVs across the verticals who are trying to rent professional Software Testing groups. Few differentiators of our security testing offerings are:
TGGTECH’S SECURITY TESTING THOUGHT LEADERSHIP

Data Breach and How Security Testing Helps

Security Testing Tools- Experiences and Recommendations

Top Automobile Financing Firm in United States leverages TGGTECH’s Security Testing Services to create hack-proof applications




